REVIEW ARTICLE
SANTOS, Levi Alves dos [1]
SANTOS, Levi Alves dos. Ransomware attacks and the protection layer on government systems. Revista Científica Multidisciplinar Núcleo do Conhecimento. Year. 07, Ed. 08, Vol. 04, p. 132-161. August 2022. ISSN: 2448-0959, Access link: https://www.nucleodoconhecimento.com.br/technology-en/ransomware-attacks
ABSTRACT
Ransomware is malicious software used for hijacking and encrypting personal, business or government data, following this theft/blocking a ransom demand through cryptocurrency, whose tracking is impossible. As a guiding question is the question: what are the best practices in Information Technology Systems Management and how can they collaborate to mitigate ransomware attacks? The purpose of this article is to present multiple cases of ransomware attacks on the electronic systems of different large companies in the United States and the existing preventive means to mitigate such risks. This original article was developed by adopting the methodology of bibliographic research, to discuss malicious electronic programs (malware) in the explained pattern. The main conclusions found were: need to adopt good practices related to security and information management; investments in high-level security systems for local or remote network protection; investments in professionals specialized in Information Technology and holders of solid knowledge in ransomware; standardization of uses and practices in the use of organizational devices; elaboration and storage of systemic backups; awareness of individuals and companies about non-payment of ransoms.
Keywords: Cyberspace, Cyber Crime, Ransomware.
INTRODUCTION
Information is currently the most powerful resource for individuals, organizations and state institutions. According to Brito (2016, p. 8), information, over time, has come to represent an important capital in the context of organizations, as well as governmental institutions, and in the personal sphere. With regard to the commercial scope, improper access by third parties to a company’s confidential information can lead it to failure in its market segment, as well as in the financial sector.
In this perspective, cyberspace is a structure whose territoriality has been built at a global level, based on the Information Society. Its dynamics include the relationships between local and global spaces, carried out through “information and cooperation networks of the most varied natures”, relying on its physical structure and the flow of information possible for the formation and functioning of virtual communities made possible by the internet (SILVA, 2014).
The incidence of large-scale ransomware attacks on US companies from 2017 onwards will be presented, based on the presentation of the different cases, with and without ransom payment. In addition, the different types of malware and effects that operate on the devices of its victims were listed.
As a guiding question is the question: what are the best practices in Information Technology Systems Management and how can they collaborate to mitigate ransomware attacks?
The purpose of this article is to present multiple cases of ransomware attacks on the electronic systems of different large companies in the United States and the preventive means that currently exist to mitigate such risks.
The present bibliographical research will bring a brief timeline related to the emergence of the internet, the advancement of Information Technologies and devices, the emergence and evolution of malicious virtual programs, the biggest cyber attacks that occurred in the last decade against North American companies, and a list of security measures that, together, make up the best practices in this segment.
THE ADVENT OF THE INTERNET
In the interval between 1947 and 1991, the Cold War arises, a non-armed conflict, but of a political-ideological character, between the two greatest world powers, at the time, the United States of America (USA) and the Soviet Union (USSR), dividing the global village into two groups that represented, respectively, capitalism and communism (SILVA, 2022).
At that moment, the need for agile, safe and effective communication emerged, which was developed by the public administration of the United States to enable the interconnection between universities and research centers (SILVA, 2022).
The internet was born, which became popular in the 1990s, through the emergence of Information and Communication Technologies (ICTs), which allowed the progressive digitization of different types of materials and documents (SILVA, 2014), in addition to designing electronic media as a new option for agile communication in the integration between governments and citizens, through “innovation, rationalization and adoption of management models that prioritize the availability of information and services to citizens (MEDEIROS et al., 2020, p. 652).
For Medeiros et al. (2020, p. 651), cyberspace dominates human interactions, being an artificial space, however, constituted by “unique peculiarities, which was formed from the interconnection of physical layers (people and machines) with digital layers (software and information)”.
With regard to the Information Society, Marietto (2001) teaches that it is composed not only of a certain delimited physical space, but also of that experienced by communities, whose communication environment is precisely cyberspace.
To define this concept, Marietto (2001, p. 32) reports the definition of Irvine (1998), when he explains that it is “an imaginary layer of networks located on top of the physical structure of cities, a layer that involves the ‘space economy and the global infrastructure’”, mentioning that the composition of this material space also takes place through the telephone, telegraph, fax, computer networks, etc.
The term cyberspace appears in the science fiction book entitled “Neuromancer”, authored by William Gibson, in which cyberspace is attributed to the “conception of an artificial environment where data and social relations travel indiscriminately, that is, it is a non-physical space in which a consensual hallucination can be experienced at all times by its users” (SILVA, 2014).
For Marietto (2001), cyberspace has promoted changes in concepts related to space and time, which are gradually being adapted to the new world reality, since physical structures and information flows are being designed, represented by cybermaps, which demonstrate: the number of hosts in each spatial unit; the number of computers with internet access; the number of registered domains and the number of telephone users.
In turn, Silva (2014) reports the definition given by Manuel Castells (2000) regarding the formation of new cultures from new communication processes, which are also based on the consumption of different signals, allowing the mixing of human behavior within virtual reality. It should be noted that cyberspace is realized through a gigantic technical infrastructure, involving the telecommunications area and the tangle of cables, wires, networks, computers, etc.
As a sample of the volume and speed of the attacks, two links are indicated here that allow their visualization in real time, they are: on the SonicWall website: https://attackmap.sonicwall.com/live-attack-map/; and a second indication would be on the Fireeye website: https://www.fireeye.com/cyber-map/threat-map.html.
It’s an impressive move.
WHAT IS A RANSOMWARE?
According to Oliveira (2018), with the creation and evolution of different software, with specific characteristics, that is, they are broad and open, they are creations that allowed the existence of vulnerabilities, which together with possible hardware failures, bring together loopholes for entry attacks on your systems, known as cyberattacks.
Thus, with regard to cyber crimes, Philot (2021) explains that the internet is an unlimited frontier that brings together individuals, companies and government entities arranged flat, given the access gained from then on.
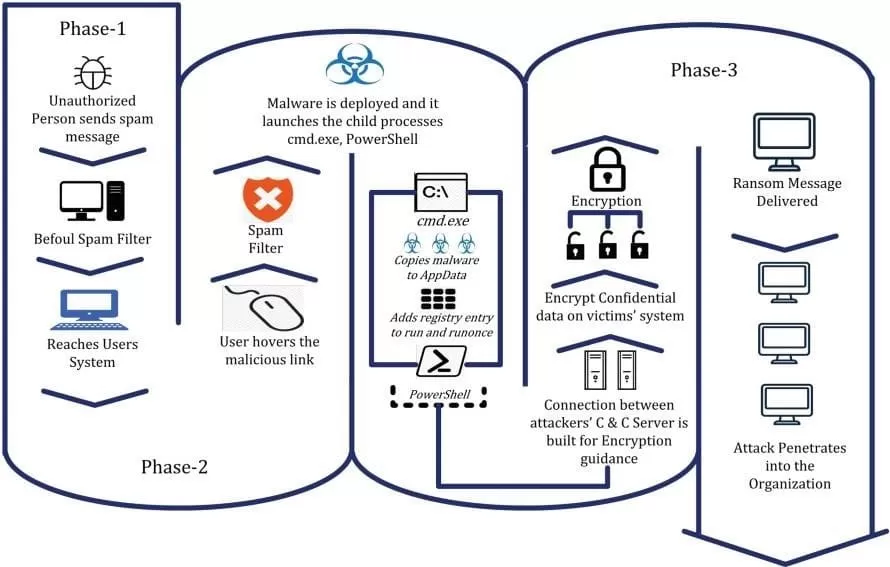
The term ransomware emerged from the merger between the words ransom (rescue) and malware (malicious program), and has been used to explain a class of malware whose purpose is to block, hijack and scramble personal and financial data existing on electronic devices, with the aim of to extort their victims (LEMA and FREITAS, 2021).
With the objective of illegally infiltrating a certain computer system of others, the infection of a certain device by a ransomware aims to cause damage and block the system in question and all the information contained therein, in order to ask for monetary ransom through cryptocurrencies, which is an untraceable virtual currency, as there is no state control.
According to Fornasier (2020, p. 209) ransomware emerged around 1990, when Joseph Popp discovered malicious codes intended to infect different computers. Pimentel (2021) describes that these groups constituted the new crime industry.
The success in obtaining cyber attacks and the consequent receipt of ransoms allowed criminals to become more and more daring. Fornasier (2020, p. 209) mentions that in 2020, the operators of the Doppelpaymer ransomware launched a website to expose stolen data from different companies that are the focus of their crimes, whose victims refused to pay the ransom.
Lema and Freitas (2021, p. 6) explain that ransomware attacks initially affected the Windows platform, but that its evolution started to allow crimes also on other platforms, such as Apple, Android and Linux. Currently, they even reach smartwatch devices through the Locker ransomware.
Pimentel (2021, p. 3) reports that the initial concept of a computer virus was born around 1940, announced by John von Neumann in his article “Theory of Self-Reproducing Automata”, published in 1966. Codes were formulated to damage machines, which should copy themselves to infect new hosts.
Yet Pimentel (2021, p. 3) describes a brief timeline on the emergence of computer viruses:
-
-
- 1971 – Vírus Creeper, sem objetivo malicioso, foi criado por Bob Thomas, da empresa BBN Technologies, cuja finalidade era autorreplicar-se e ser removido do host anterior de forma automática a cada nova infecção (KASPERSKY, 2021, apud PIMENTEL, 2021);
- 1982 – Vírus Elk Cloner, o primeiro utilizado de forma massiva, atingiu os computadores populares dotados de sistema operacional da Apple II. Depois de 50 inserções do disquete infectado no sistema leitor de um dispositivo, o vírus exibia um poema na tela do aparelho infectado do usuário (AVG, 2021, apud PIMENTEL, 2021);
- 1984 – Vírus Core Wars, criado nos laboratórios Bell Computers. Era um tipo de vírus mais potente que os anteriores, que comprometia a memória RAM das máquinas; alastrou-se nas universidades americanas (MEYER, 2015, apud PIMENTEL, 2021);
- 1986 – Brain e Bouncing Ball foram os malwares capazes de infectar o setor de boot dos disquetes. Ao mesmo tempo surgiram outros vírus capazes de infectar arquivos com extensão exe e com. O vírus Brain é considerado o primeiro vírus capaz de contaminar os personal computers (PCs) (MEYER, 2015, apud PIMENTEL, 2021);
- Para combatê-lo, John McAfee desenvolveu, em 2012, o famoso antivírus McAfee, ao mesmo tempo em que abriu sua empresa homônima (AVG, 2021; OFICINA DA NET, 2015, apud PIMENTEL, 2021).
- Já o Bouncing Ball é considerado um vírus com função não destrutiva, porém, instalava-se no primeiro setor do disquete, contaminando todo o sistema conforme inseridos outros disquetes (MEYER, 2015, apud PIMENTEL, 2021);
- 1989 – Cavalo de troia AIDS (ou PC Cyborg Trojan) primeiro ransomware, desenvolvido por Joseph Frank Popp. Utilizava-se de um contador para numerar cada reinicialização do sistema operacional, até chegar à 90ª., quando então os arquivos da máquina infectada ficavam ocultos e inacessíveis para a vítima. Uma única chave era utilizada para criptografar e decriptar os arquivos, depois do pagamento do resgate. Uma vez que o criminoso fornecia uma caixa postal no Panamá para o pagamento de US $189, ele foi descoberto pela polícia, porém, sob a alegação de que seus ganhos seriam destinados às pesquisas pela cura da AIDS, foi considerado legalmente inimputável (PIMENTEL, 2021, p. 3-4);
- 1992 – Vírus Michelangelo, criado para ser inativo e indetectável até o dia 06 de março, aniversário do artista, e a partir dessa data, ele corrompia os arquivos, sobrescrevendo caracteres aleatórios (AVG, 2021, apud PIMENTEL, 2021, p. 3-4);
- 1999 – Vírus de macro Melissa, criado por David L. Smith, considerado o primeiro a empregar engenharia social para ser espalhado, que ocorre por e-mail, partindo de um dos contatos da vítima (AVG, 2021, apud PIMENTEL, 2021, p. 3-4);
- 2000 – Vírus Iloveyou infectou milhões de usuários do Windows, incluindo o Pentágono e a CIA. Era difundido por um e-mail com um arquivo anexo denominado Love-letter-for-you, que, ao ser executado, retransmitia a mensagem para todos os contatos do usuário (AVG, 2021, apud PIMENTEL, 2021, p. 3-4).
-
Between 1989 (creation of AIDS) and 2005, little significant ransomware attacks were recorded, regaining strength only in 2005. During the period before the emergence of bitcoin (in 2007), it was possible for investigations to trace the payment of ransoms; however, as of 2017, the attacks returned with much greater force and frequency (PIMENTEL, 2021).
Brito (2016, p. 16) explains the occurrence of some cases between 2005 and 2006 pointed out by Trend Micro, in Russia, when verifying a “compression of some types of files and overwriting them with the zipped file with a password”. Simultaneously, a text file was created that informed the user that his data had been hijacked, which could be released to the victim upon payment of US$ 300.00.
With the popularization of this new criminal commercial activity, as of March 2012, Trend Micro verified the spread of cases across Europe and North America, when, then, a new type of ransomware emerged that encrypted (scrambled) files at the same time as which blocked the operating system of the affected device (BRITO, 2016, p. 16).
Figure 1 – Image representation of information blocking

Encryption aims to lock the stolen file, tricking the victim into paying the ransom. However, it should be noted that cryptography can also be used legitimately, in order to “protect user privacy and confidentiality” (KOK et al., 2019, p. 2). To this end, there is a definition regarding the limit on the frequency of encryption, which differentiates its legal action from the illegitimate.
Philot (2021) explains that the term malware covers different categories of spy applications, with spyware being used to monitor user behavior and steal their data, while ransomware captures the system, encrypting files and demanding ransom for them.
Such characteristics made these malwares called CryptoLocker, in 2013. That same year, crypto-ransomwares known as CryptoDefense or Cryptorbit entered the scene, with the purpose of encrypting “databases, web files, office, videos, images, scripts , texts and other non-binary type files, with subsequent deletion of existing backups” (BRITO, 2016, p. 16).
Figure 2 – CryptoLocker Infection Chain
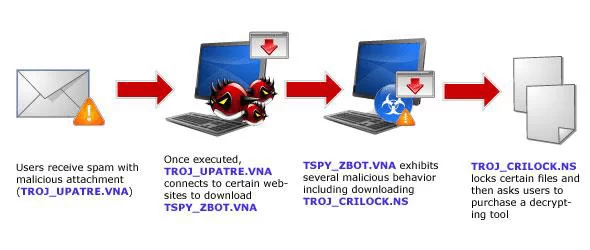
Since ransomware was invented, it has attracted more and more cybercriminals, due to its high rates of return and profitability, with more improved versions being gradually created (KOK et al., 2019).
Its emergence and expansion were greatly facilitated through a business model that could be found on the Dark Web. This is Ransomware-as-a-Service (Raas), also known as a ransomware kit, whose operation consists of the sale of this kit by a hacker, charging a monthly fee for the sale, or a part of the profit from the scams, which can vary from 20% to 50% (GAFETY, 2021).
Lema and Freitas (2021, p. 4) defend the existence of two basic types of ransomware in circulation, they are “crypto ransomware and locker ransomware”. Crypto ransomware is used to scramble (encrypt) certain types of data files and personal files, while locker ransomware works by locking the computer and preventing its use. In both cases, hackers try to force their victims to pay the ransom through online payment channels, using keys for decryption.
Kok et al. (2019) defend the existence of three types of ransomware, as shown in Figure 3.
Figure 3 – Types of ransomware
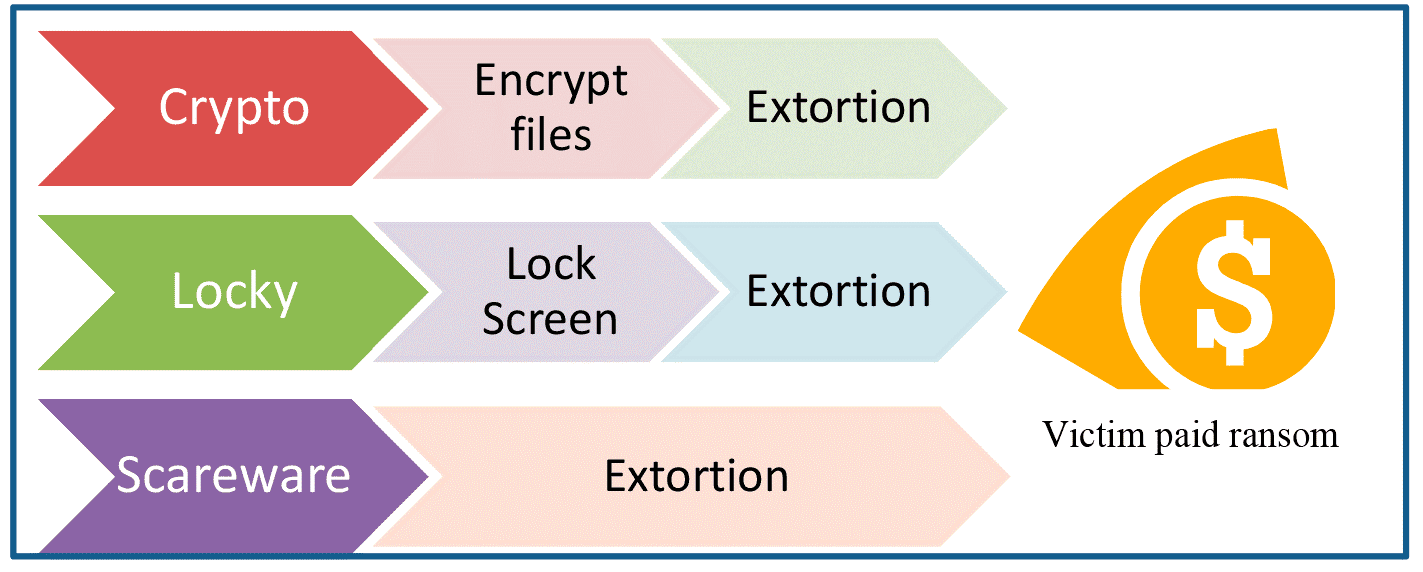
According to Kok et al. (2019, p. 2), each of the 3 types of ransomware can be defined as follows:
1st. type – scareware. He imitates an authority that seeks to alert his victim and ask for payment, under penalty of legal denunciation. In practice, it does not represent any real danger, as it only serves to scare, with the intention of obtaining the payment of the ransom. In the same modality, there is leakware, used to threaten its victim in exposing the crime (not committed) to their friends and family.
2nd. type – locker-ransomware (or locker-restorer). Ransomware that locks down victim’s system when they access the login page. Considered by experts to be mildly dangerous, it can be resolved by the victim by restarting the system in safe mode.
3rd. type – crypto-ransomware – this is a highly dangerous malware, as it scrambles the victim’s files, and with that, prevents access to data without decryption.
When accessing the victim’s network, the phishing scam allows the theft of documents before carrying out their encryption, in order to obtain information and customer data considered “sensitive”, including personal data and financial records, with small samples being provided to the victim (s) victim(s), in order to convince them to pay the ransom, a practice considered “double extortion attack” (BRANCO, 2021).
At the same time that the criminal group provides the victim with free access to up to three files, proving that the restoration will actually take place, this group directs its victim(s) to a chat where they intend to carry out the negotiation, chat installed on the website Tor, “where communications are 100% anonymous” (BRANCO, 2021). The attempt to convince the victim to pay consists of blackmail on the public availability of stolen documents, if payment does not occur.
Figure 4 – Image of the Ranzy Locker payment site
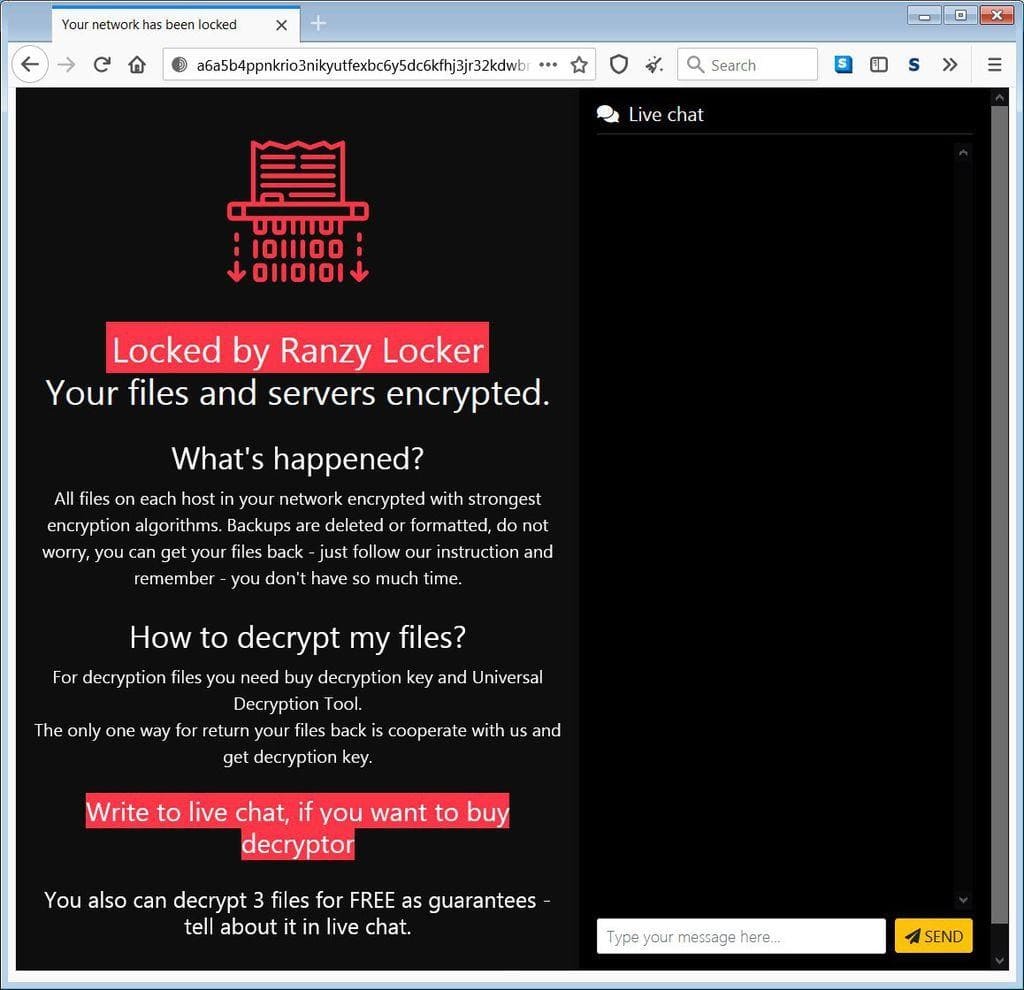
There are other ways to promote electronic attacks, causing general panic to victims, whether individuals, legal entities or government institutions. A simple Domain Name Service (DNS) change, which consists of the deviation of the original Internet Protocol (IP) address, promotes the redirection of the query in progress to another IP, which does not correspond to the servers under attack. A “defacing” is performed – that is, a page that replaces the original with the message from the hacker group” (ALECRIM, 2021A).
It is a DNS Spoofing, or a “DNS cheating” (ALECRIM, 2021A). As a more elementary scam, it acts as follows: the user enters the address of the website he wants to access, only that, by bypassing the DNS, it will be taken to the DNS of the criminal group.
According to Carvalho and Pelli (2017, p. 99), in general, the different devices that connect to the internet have free access to DNS services to define domain names. Since there are no restrictions for packages of this type of service to be made available, it becomes a service susceptible to ransomware attacks.
DNS Spoofing attacks are considered highly dangerous, given the lack of studies and research for appropriate protective solutions Carvalho and Pelli (2017).
Among the variations regarding the type of attack are: IP Spoofing, which is easy to camouflage on the internet; the IP address is spoofed, suggesting that it is a trusted address, allowing the criminal to gain unauthorized access to a particular device or network; it is ransomware that is easily camouflaged on the internet (CARVALHO and PELLI, 2017, p. 100).
DNS Spoofing manages to trick the victim’s device, redirecting their requests to a page of interest to the malicious user. Its action takes place in four steps: 1. the target user makes a request to the DNS server; 2. the attacker returns a fake IP to the target user’s request before it arrives at the DNS server’s response with the real IP; 3. the DNS server response with the real IP is received and discarded by the target, as a response has already been received before; 4. the user accesses the address provided by the attacker (CARVALHO and PELLI, 2017, p. 100).
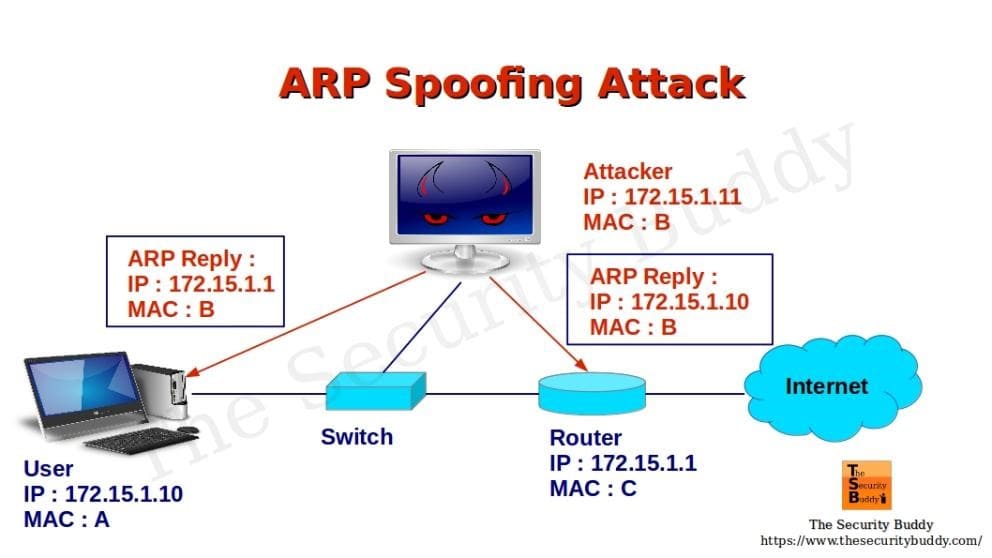
In turn, ARP Spoofing changes the response sent to an original request, sending the user a false Address Resolution Protocol (ARP) response. With this false response, the data sent by the victim’s router will be sent to the malicious user (CARVALHO and PELLI, 2017).
Figure 5 – Image representation of an ARP Spoofing
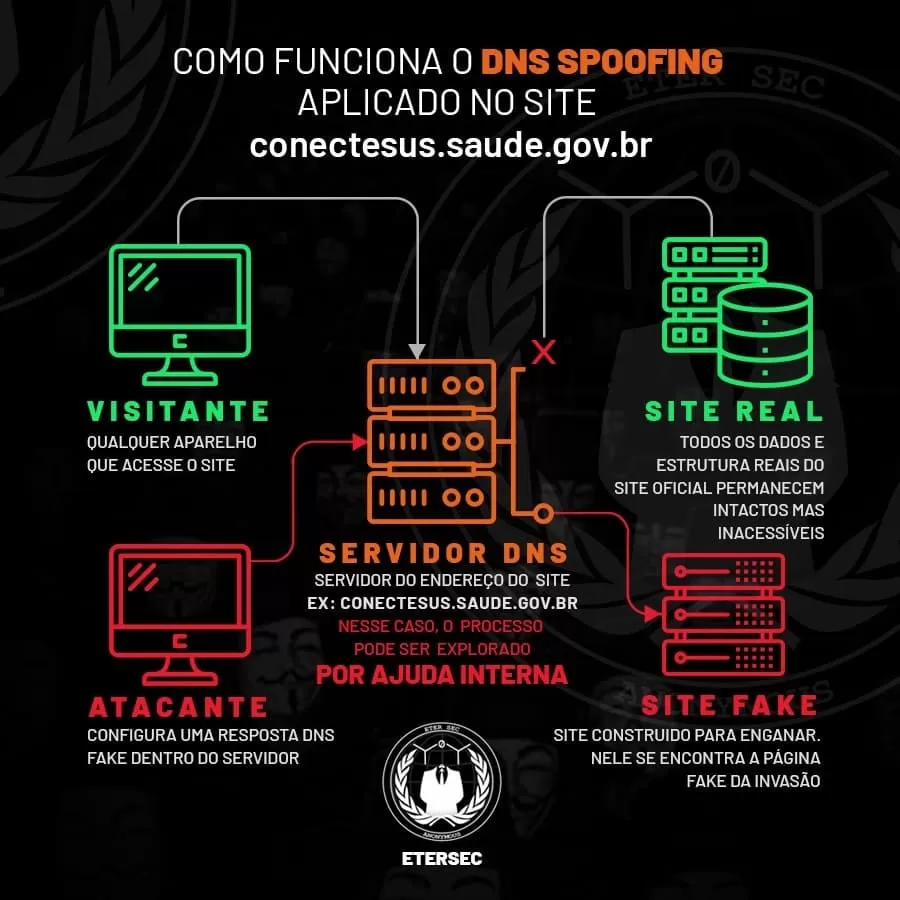
If we take as an example the recent attack on the Brazilian Ministry of Health portal, reported as ransomware, but analyzed by the Anonymous group, in its collaboration with explanations and graphics, it was found that, in fact, what happened was a DNS redirect of that MS, proven with a basic explanation given by the Anonymous group (MARTON, 2021).
This analysis consisted of observing a false trail given by criminals, when they reported having downloaded 50 tb (terabytes) of data from that Ministry, whose IP is hosted in Japan. It is a transfer considered impossible to be performed on high traffic servers in a short time, in addition to not having been given samples of recent information (ALECRIM, 2021A).
The DNS bypass in this case was demonstrated by the Anonymous group, as shown in Graph 1.
Graph 1 – DNS deviation
The solution found by the criminals was to remove the defacer, as there would be no way to restore the data, because it would not have been stolen.
NORTH AMERICAN ELECTRONIC SECURITY BODIES
Personal and financial data and information of an individual/company/institution are fundamental elements to be protected. This protection implies “in confidentiality, integrity and availability, which constitute the three pillars of information security” (PHILOT, 2021, p. 9).
Confidentiality involves privacy over sensitive information, as it refers to the need for any data to be out of reach of unauthorized persons; in addition, all information must remain intact.
Figure 6 – Image representation of a rescue attack
The United States Cybersecurity and Infrastructure Security Agency (CISA) works together with the Federal Bureau of Investigation (FBI), regarding the occurrence of electronic crimes in the United States (BRANCO, 2021). In October 2021, the FBI warned the US government about the occurrence of at least 30 attacks that year, carried out against local companies in the areas of technology, transportation and information. In addition to monitoring the occurrences, CISA and FBI also indicate ways of identifying attempts of this type of threat.
According to the FBI, among the groups involved is Ranzy Locker, whose kidnapping notice resembles scams carried out by two other ransomware groups ALO and ThunderX, apparently missing, which, possibly, came together to operate as Ranzy Locker (WHITE, 2021).
The invasion of different systems consists of brute-force attacks or phishing scams, through which criminals try to use random credentials until they gain access, or by assessing vulnerabilities to steal Microsoft Exchange email passwords, program that allows access to users’ emails even if disconnected from the internet (BRANCO, 2021).
Figure 7 – Ranzy Locker Hijack Warning Message
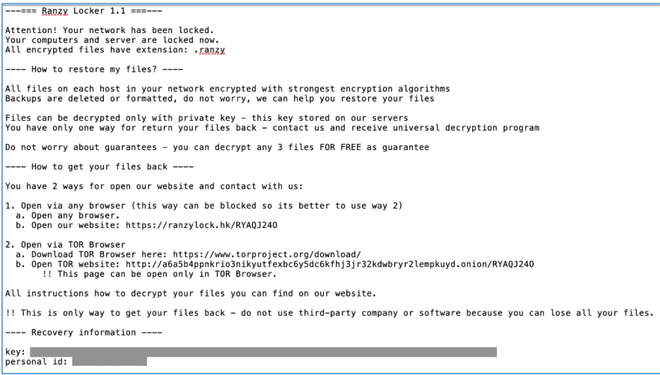
As far as US law is concerned, since different US laws are statewide. Masseno and Wendt (2017) refer that section 523 of the California Penal Code provides for the classification of the crime of extortion, where the freedom of life to dispose of its assets, in relation to its devices, as well as its confidential information is guaranteed.
However, in March 2022, a new law was passed by the US Senate on the defense of companies and institutions that suffer from any cyber attack. It is a joint effort between Republicans and Democrats, aimed at protecting critical infrastructure areas, as well as the nation’s economy (TIC NEWS, 2022).
It is considered “common-sense, bipartisan legislation that will help protect critical infrastructure from relentless cyberattacks that threaten both our economy and our national security,” according to Gary Peters of the Senate National Security Commission (TIC NEWS, 2022).
From the new law, all critical infrastructure operations are obliged to alert the Department of Homeland Security within 72 hours of the occurrence of any attack suffered, in addition to informing within 24 hours if you have made the ransom payment to access again the stolen data (TIC NEWS, 2022).
RECENT CYBER ATTACKS IN THE UNITED STATES
Large US companies and government systems have been the most frequent targets of hacker attacks, which use malware capable of blocking systems to the point of demanding large amounts of data for ransom. Medeiros et al. (2020) refer to recurrent criminal actions to block, steal and demand ransoms payable through cryptocurrencies, which cannot be traced.
Medeiros et al. (2020, p. 653) report that cyber criminals prefer “public websites, which operate in the creation of clones simulating the addresses of official websites”. These authors refer to several hacker attacks that occurred against North American institutions, the consequences and solutions adopted at that time.
Regarding the way in which ransomware invades a business system, Sophos, a British developer and supplier of security software and hardware, including antivirus, antispyware, antispam, network access control, encryption and prevention software of data loss for desktops, servers for protecting email systems and filtering for network gateways, tabulated the forms and percentages of the incidence of cyber intrusions, as shown in Table 1.
Table 1 – Ransomware entry forms in %
| HOW RANSOMWARE ENTERS THE ORGANIZATION SYSTEM | % INCIDENTS |
| Via file download/email with malicious link | 29% |
| Via remote attack on the server | 21% |
| By email with malicious attachment | 16% |
| Incorrectly configured Public Cloud instances | 9% |
| Through our Remote Desktop Protocol (RDP) | 9% |
| Through a supplier that works with our organization | 9% |
| Via USB device/removable media | 7% |
Source: Pereira and Neves (2021, p. 75).
In turn, the data tabulated in 2020 by Coveware, a company specializing in cybersecurity and protection and recovery from electronic scams, shows a high volume of ransomware ransom payments by large North American organizations, causing an upward projection in the suggested values in the subsequent actions of these criminal groups (PEREIRA and NEVES, 2021). Graph 2 shows the increase in redemption payments by 31%, reaching the amount of US$ 233,817.
Graph 2 – Quarterly Ransomware Ransom Payment Average
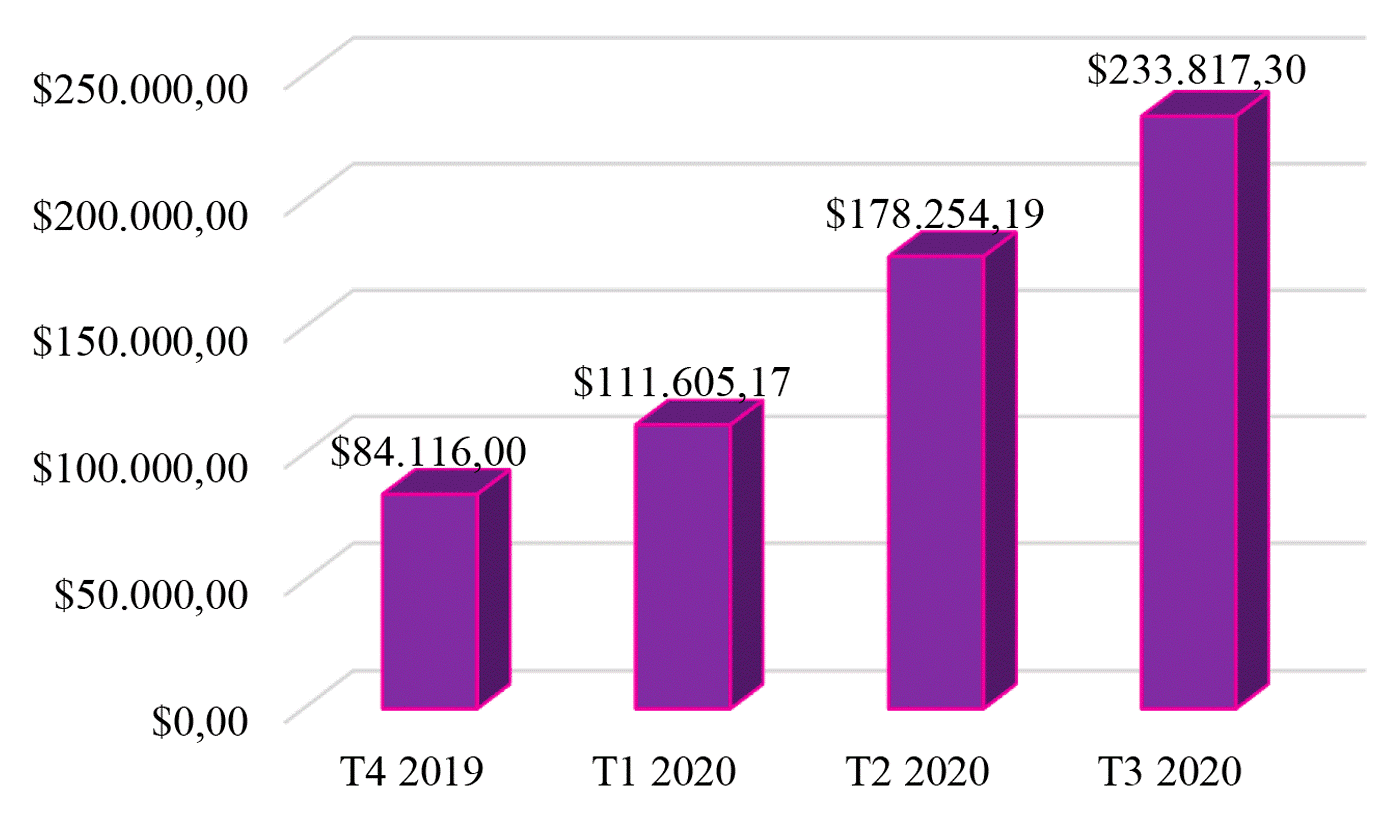
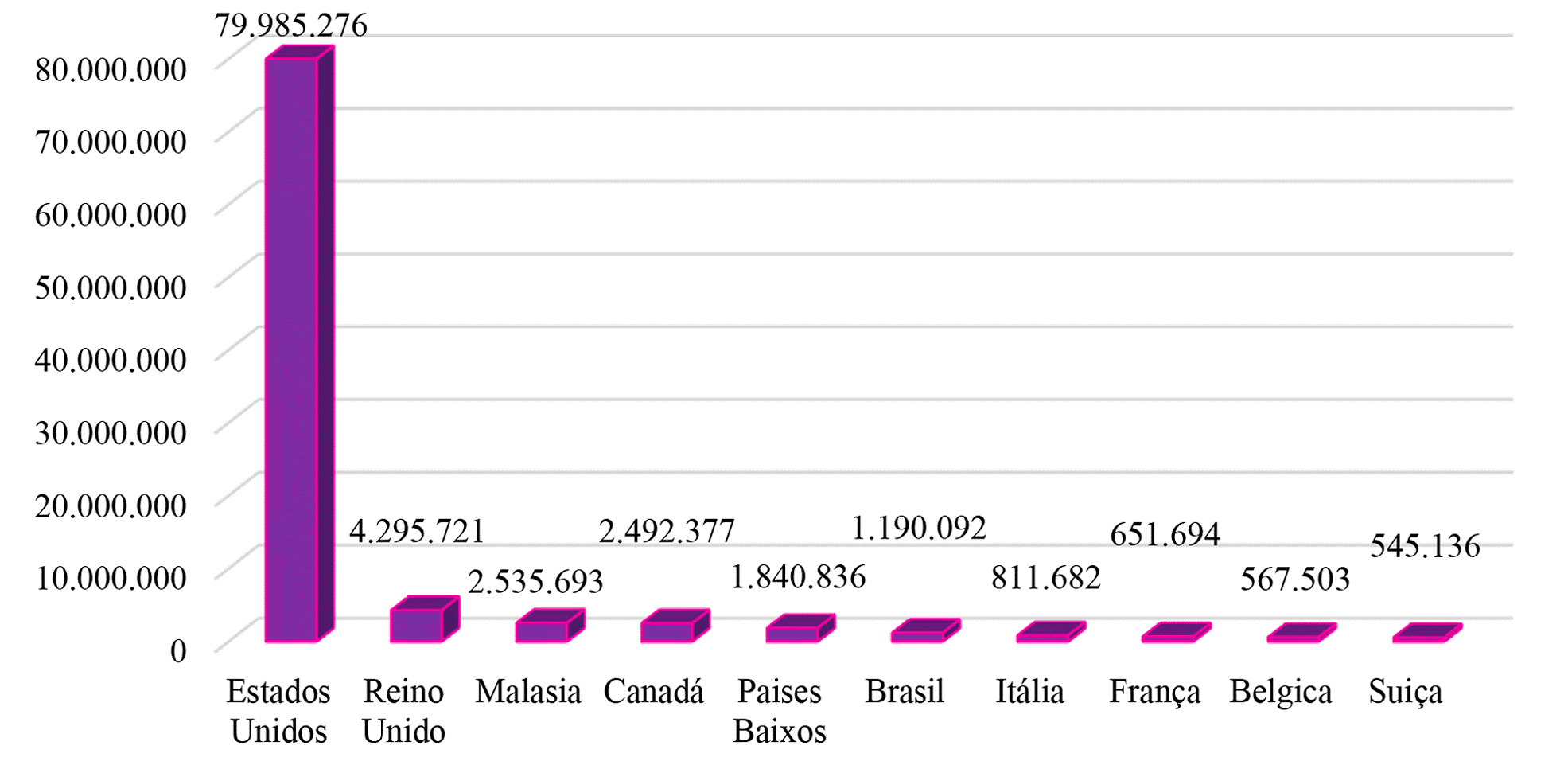
SonicWall, a company specialized in creating, scaling and managing security in cloud, hybrid and traditional environments, prepared a report on cyber threats that occurred until July 2020 in different countries, as shown in graph 3 (PEREIRA and NEVES, 2021).
Graph 3 – Ransomware attacks in 10 countries up to July 2020
In order to present the cases that occurred in recent years in the United States, the main cyber attacks on companies and institutions are now reported here.
In May 2017, the WannaCry ransomware attack took place, considered the biggest of all time, affecting computers in different parts of the world. This malware targeted Microsoft Windows system installed on different types of devices. Medeiros et al. (2020) explain that it was cybercrime that caused billions of dollars in financial losses, starting to be considered, from then on, the great lesson to what was called “digital literacy”, in the sense of the adoption of systematic backups.
WannaCry ransomware was considered a malware that caused a true “global epidemic that happened in May 2017, spreading through computers that had the installation of Microsoft Windows”, to be released only upon payment of ransom in bitcoins. This cyber-attack was possible, in part, due to the lack of habit in updating the software installed on the thousands of computers that use the aforementioned system (KASPERSKY LAB, 2022A).
Kumari et al. (2019) report that WannaCRy ransomware affected devices on a large scale, reaching machines in 150 countries in less than 24 hours, targeting Microsoft’s Windows operating systems. The ransom ranged from $300 to $600, to be paid in bitcoins. As the attacks progressed and ransoms were paid, that amount reached $1,077, according to the 2017 Symantec Report.
Among the victims of this malware are the British National Health Service, the international shipper FedEx, Telefonica, among other large companies. In addition to these, the systems of the police department in India and several local businesses were undermined. The countries affected by WannaCry, on the other hand, can be mentioned Spain, Portugal, Russia, Ukraine, and Taiwan (KUMARI et al., 2019).
Given the seriousness of this crime and the publicity achieved by this contamination, some investigations were initiated. A security bulletin issued by Kaspersky Lab assures that, in 2016, approximately 20 companies paid the ransom, without ever receiving their documents back. In turn, IBM[2] found that 70% of the administrators it investigated reported that they would have paid the ransoms, while Osterman Research reported that the total amount of ransom payers was minimal (KUMARI et al., 2019).
The big question that allowed all these cyber crimes is due to the projection of bitcoin, which, being an untraceable currency, provided increasingly boldness to these criminal groups (KUMARI et al., 2019).
In March 2020, the new coronavirus testing center at the University Hospital of Brno, in the Czech Republic, was targeted by ransomware. “Criminals gained access to the hospital system and encrypted the databases (NEWMAN, 2020; ARBULU, 2020, apud MEDEIROS et al., 2020, p. 653).
Once the management of that hospital decided to face the crime by refusing to make the ransom payment, the solution was to temporarily suspend care, through the reassignment of its patients to other medical services (MEDEIROS et al., 2020).
Also in March 2020, the system of the Public Health District of Champaign-Urbana (Illinois) was also targeted by ransomware, harming that medical service. Since it had an updated backup of its electronic data, it was possible for this health service to decide on the refusal to pay any ransom, and its data was only slightly affected by the action of the criminals (MEDEIROS et al., 2020, p. 653).
On May 7, 2021, a cyberattack was carried out against the company Colonial Pipeline, an oil company responsible for supplying approximately 2.5 million barrels of oil that circulate daily through the pipelines of that organization, which is responsible for supplying 45 % of diesel and gasoline for the entire east coast of the United States (ALECRIM, 2021B).
As a result, there were long queues at gas stations, rising prices and the partial or total stoppage of services. Fuel supplies were interrupted for a few days, leading the US government to declare a state of emergency in that region on May 9 (ALECRIM, 2021B).
Upon cybernetic invasion, the company’s management ordered the shutdown of most of its systems, in an attempt to contain the growth of that attack. In order to contain the scale of the situation, and in view of the pressure suffered to normalize the supply, Colonial Pipeline decided to pay the amount demanded, set at 75 bitcoins by Dark Side, a value that corresponded, at the time, to US$ 5 million. This decision allowed the normalization of the company’s electronic systems in a few days (ALECRIM, 2021B).
Investigations promoted by the FBI allowed a good part of the ransom paid in June of that year to be recovered. In addition, they allowed the discovery of clues about other cyberattacks that occurred in the first quarter of 2021, which hit countless other companies, whose results may have reached the US$ 50 million mark (ALECRIM, 2021B).
For these reasons, the US government released the offer of a reward in the order of US$ 10 million to specialized groups that could collaborate with information about DarkSide members, which apparently ceased its activities. It is speculated that its members may have founded a new group called BlackMatter (ALECRIM, 2021B).
At the end of May 2021, the multinational JBS, which operates in the processing of beef, pork, sheep and chicken, and in the processing of leather, suffered a cyber attack on its servers in the United States and Australia, ultimately deciding to pay of a total ransom of US$ 11 million (LAVADO, 2021).
After paying the ransom, the company made public the information that the company’s backup servers were not affected, further disclosing taking “immediate action, suspending all affected systems, notifying authorities and activating the company’s global network of IT professionals and third-party experts to resolve the situation”. Finally, he explained that the decision to pay the ransom was due to the possible delay in “certain transactions with customers and suppliers” (LAVADO, 2021).
In October 2021, a DDoS (Distributed Deny of Service) hack was committed against the United States Department of Health and Human Services (HHS), which is the US Department of Health and Human Services. The Southeast Florida health system hack had access to approximately 1.3 million people, comprising data such as ID numbers, patient medical histories and banking details exposed in the Broward Health hack, which is a network comprising more 30 units and serves around 2 million patients in Broward, Florida (LYNGAAS, 2022).
The DDoS attack, also known as the distributed denial of service attack, consists of sending numerous access requests until the specific capacity limit applicable to all network resources is exhausted, including the infrastructure that allows the website to function properly particular organization/institution. In other words, to promote the sending of exaggerated requests to a website, the criminal establishes a zombie network of infected computers, controlling all the actions of each machine to promote the overload (KASPERSKY, 2022B).
Figure 8 – Image representation of a DDoS attack

As a result of the disclosure of this fact, the aforementioned cybercrime led users of the North American health system to seek secure information about the Covid 19 pandemic in other sources, avoiding consulting the official website of that body, for fear of the theft of their data. (MEDEIROS et al., 2020).
In December 2021, a second case refers to Lincoln College, founded in 1865. It was a university that promoted great achievements in the country, including the US Constitution, the achievement of individual civil rights, in addition to generating professional opportunities in the country rural environment in the state of Illinois (PRIVACY TOOLS, 2022).
According to the magazine PPlware (2022), specialized in news and information in the technological area, Lincoln College is an “institution that has overcome very difficult economic and social periods that were transversal to the whole world, such as the two World Wars, the Influenza Spain or the Great Depression, but was not able to withstand a ransomware computer attack, after two years of pandemic”.
Despite the digital advances made for its operating system, Lincoln College has failed to invest in cybersecurity. With this, in addition to the Covid 19 drama, in December 2021, he was the victim of a certain type of ransomware used to invade his systems, which, having their servers and data blocked, being prevented from identifying approximately 600 students who would make their enrollments, as well as donations (PRIVACY TOOLS, 2022).
Even with investments of the order of “US$ 100,000 to revitalize the databases and stop further attacks, the resource used was not common malware but potentially destructive software”, it took just four months for that institution to close, after 157 years of activities (PRIVACY TOOLS, 2022).
In January 2022, it was the turn of the Bernalillo Detention Center, the most populous county in New Mexico. A cybernetic invasion took place that left all the security cameras and door opening and closing mechanisms down, between 00:00 and 5:00 in the morning. In addition, all data containing the complete personal information of detainees and crimes committed were unavailable (TECMUNDO, 2022).
Figure 9 – Bernalillo Detention Center (New Mexico)

Until the technical solution was implemented, visits were suspended, the detainees were kept in their cells, requiring the use of manual keys to open or close the necessary doors.
In turn, there are cyber crimes to video conferencing applications. The idea is unanimous on the fact that no communication application is 100% secure regarding the confidentiality of the information they contain, including files in clouds, since clouds are physical servers located in different countries, as demonstrated by the Snowden case, for example (MEDEIROS et al., 2020, p.655).
Another vulnerability of video calling applications is the possibility of cybercriminals listening to communications that occur during a given conference, creating embarrassing situations, when trying to close the meeting or classroom, for example, or even transmitting racist and/or pornographic messages. Among the different occasions, we can mention the exhibition of “photos of meetings on social networks, showing the caller’s identification code, as the British Prime Minister, Boris Johnson, did at the end of March” (MEDEIROS et al., 2020, p. 655).
IMPROVEMENTS IN INFORMATION SECURITY MANAGEMENT
According to the portal Tecmundo (2022), ransomware attacks are considered “the biggest cyber threats to private companies and public institutions in the USA”. This statement came when Tecmundo reported data computed by Forcepoint, an American multinational developer of computer security software, data protection, cloud access security broker, firewall and cross-domain solutions.
This survey conducted by Forcepoint tabulated numbers as to how 75% of security professionals believed that new malware and ransomware attacks would grow on organizations in the next 12 months. According to a US Treasury report on a possible record of ransomware payments that year, a task force was created in the country to fight these crimes in 2021 (TECMUNDO, 2022).
In turn, CISA released a list of electronic bad practices, which are: use of single-factor authentication; use of unsupported (or end-of-life) software; use of known/fixed/standard passwords and credentials (OWAIDA, 2021).
Among the various possibilities of effective protection of your operating systems, the following are indications gathered from different sources.
Brito (2016, p.12) refers to the importance of Information Security Management. He explains that companies and institutions are always looking for solutions to mitigate cyber crimes, an activity on the rise. It is about identifying and implementing good practices that aim at the effective protection of data and business and governmental systems, through public policies, also counting on the definition of specific roles and responsibilities.
Owaida (2021) reports the recommendations developed by CISA, about companies adopting Multi-Factor Authentication (MFA) as a more secure option, as it provides “an extra layer of security and makes it exceedingly difficult to carry out attacks on user accounts” . This author refers to the satisfactory results obtained by using the MFA, reported in a study carried out by Google, in partnership with the University of New York and the University of California.
According to Cisa, such a study demonstrated that “the use of MFA resulted in the blocking of 100% of automated bots, 99% of mass phishing attacks and 66% of attacks targeting Google user accounts” (OWAIDA, 2021).
Among the different multilayer systems, Kok et al. (2019, p.3) refer to RansomWall, whose last layer uses “Machine Learning to predict the result of features collected in static analysis, dynamic analysis and trap layers”. It is considered a method with a high detection rate, whose “rate reaches 98.25% and almost zero false positives using a Gradient Tree Boosting algorithm”.
There is also AntiBiotics, which is based on authentication and applications, being used to control access to different files on a given device. It is considered effective, since denying access to files can prevent ransomware from capturing the file (KOK et al., 2019, p.3).
Regarding the search for system anomalies, monitoring processes and specific file directories must include a processor, memory usage and I/O rates, whose operations are performed by various external devices, allowing the transfer of data between the external environment and the computer. When an anomaly is detected, the user receives “a message to remove the rescue suspect” (KOK et al., 2019, p.3).
Traps called honeyfiles can also be created, which have two functions: to attract the attack to a file that is not the real one, and the second, to analyze the type of attack, thus allowing a better understanding of the existing threats, and the elaboration of a plan for eliminating new threats (KOK et al., 2019).
Kumari et al. (2019) explain that it is possible to break the symmetry between the vision of an antivirus analyst and the ideas and action processes of criminals. This is the use of the public key concept of cryptography. While the antivirus analyst is aware of a public key existing in certain malicious software, the criminal sees the public key and also the corresponding private key, which is outside the malware, since this attacker was the creator of the key pairs.
Yet Kumari et al. (2019) mentions that individuals, companies from different branches or government institutions can be the target of different types of cyberattacks, and there is also a list of different types of ransoms: CryptoLocker, CryptoLocker.F and TorrentLocker, CryptoWall, Fusob, WannaCry , Petya, Bad Rabbit and SamSam.
Among the different approaches to enable the analysis of the various types of malware, for example, the use of the Randep method to map the behavior of malware. Each ransomware attack consists of three phases, they are: “in the first phase, stealth operations occur, in the second, suspicious activities, and in the third, the obvious actions are taken” (KOK et al., 2019, p.3).
The analysis of ransomware must be done through two approaches: “static analysis, which verifies the malware source code, and dynamic analysis, which verifies the actions of the malware after its execution” (KOK et al., 2019, p.3). The RanDroid method aims to identify threats in the form of text or image, from some application code.
With regard to Spoofing attacks, through the study carried out by Carvalho and Pelli (2017, p.99), it was found that the application of characteristics selection and pattern classification techniques to detect DNS Spoofing in local networks of computers, highly positive results were found, “whose average was 98.33% ± 0.64% in the detection in the network failure class, that is, when they were under DNS Spoofing attack”.
In turn, Branco (2021) reports the instruction manual published by CISA, suggesting good protective practices that collaborate to prevent new cybercrimes:
- Make frequent data backups, keeping them in an offline environment protected by encryption;
- Create a basic cybersecurity plan to respond to incidents, maintain operations, and communicate about steps to take;
- Use proper remote access settings, conduct frequent vulnerability scans, and keep software up-to-date;
- Ensuring everyone uses recommended security settings, disabling unused ports and protocols such as Server Message Block (SMB) when possible;
- Best cyber hygiene practices: keep anti-virus and anti-malware software active and up-to-date, limit the use of privileged access accounts, and always use multi-factor access solutions when possible.
According to Brito (2016, p. 12-13), some international standard standards were developed for the elaboration and maintenance of processes related to Information Security Management, which became known as the 27000 series. To this end, 10 applicable basic premises were listed to the different organizations, they are: Information Security Policy; Organizational Security; Classification and control of information assets; Safety in people; Physical and Environmental Security; Management of operations and communications; Access control; Systems Development and Maintenance; Business continuity and compliance management.
ISO 27001 belongs to the mentioned series. This is the international standard that specifies the Information Security Management System (ISMS), whose objective is the adoption of a set of requirements to establish, implement, operate, monitor, review, maintain and improve the ISMS, in order to implement controls that aim to properly manage the Information Security risks present in organizations (BRITO, 2016).
In addition, the aforementioned ISO 27001 is intended to ensure that all devices are maintained with adequate virtual security, requiring a permanent update of the operating system, preventing new threats, vulnerabilities and negative commercial impacts (BRITO, 2016). This standard covers companies related to industry, commerce, services, governmental and non-governmental institutions.
Among the advances made to reinforce good practices in Information Security Management, Kumari et al. (2019) highlight the antibiotic, as a mechanism for protecting ransomware, whose approach consists of several types of periodic authentication, such as biometric and human, which is done through CAPTCHA. The basic concept of the antibiotic is to adapt to the need for responses in user authentication, while maintaining the projected security levels.
CONCLUSION
The speed with which electronic resources and different technologies have advanced over time has allowed humanity to experience, in the present, highly bold positive situations, exemplified in the many possibilities brought about by globalization, in which individuals communicate and build their knowledge and receive information and news in real time.
In response to the guiding question related to the present theme, having as the question “what would be the best practices in Information Technology Systems Management and how can they collaborate to mitigate ransomware attacks?”, it has been said that in addition to the analysis of the selected literature As for theories, reported events and all the evolution we are experiencing, the work of specialists must precede the actions of criminals, through artificial intelligence, existing prevention techniques, and the development of instruments aimed at security and data protection personal and financial assets of both individuals and organizations, anticipating the next steps of criminal groups emerging from the dark web.
Among the various prevention proposals listed in this article, already adopted by experts within organizations, I sincerely believe in the need for awareness, education and training in Information Security, through the adoption of good practices described by the ISO/IEC 27001 Standard.
With this action, companies will be able to put into practice a good management in Information Technology, preventing the simplest mistakes, such as the use of weak passwords, that their employees will click on any link received from unknown emails, or click on any advertisement that appears on a particular website.
REFERENCES
ALECRIM, Emerson. PF diz que dados do Ministério da Saúde não foram criptografados por hackers. 10 dez 2021A. Disponível em:
https://tecnoblog.net/noticias/2021/12/10/pf-diz-que-dados-do-ministerio-da-saude-nao-foram-criptografados-por-hackers/; acesso em 06 jul 2022.
ALECRIM, Emerson. EUA pagam US$ 10 mi por hackers do ransomware que atacou Colonial Pipeline. Matéria publicada em nov 2021B. Disponível em: https://tecnoblog.net/noticias/2021/11/05/eua-oferecem-10-milhes-dolares-informacoes-ransomware-darkside/ ; acesso em 28 jul 2022.
BRANCO, Dácio Castelo. FBI alerta sobre ataque ransomware que afetou 30 empresas dos EUA em 2021. 26 out 2021. Disponível em:
https://canaltech.com.br/seguranca/fbi-alerta-sobre-ataque-ransomware-que-afetou-30-empresas-dos-eua-em-2021-199963/ ; acesso em 06 jul 2022.
BRITO, Douglas Roberson de. Combatendo a ameaça ransomware aplicando a norma NBR ISO/IEC 27001:2013 na gestão da segurança da informação. Monografia [Especialização em gestão de Tecnologia da Informação e Comunicação] apresentada ao Departamento Acadêmico de Eletrônica da Universidade Tecnológica Federal do Paraná. Curitiba, PR. 2016. Disponível em:
http://repositorio.roca.utfpr.edu.br/jspui/bitstream/1/19456/1/CT_GETIC_V_2015_07.pdf; acesso em 06 jul 2022.
CARVALHO, Henrique Carlos Fonte Boa; PELLI, Eduardo. Técnicas de reconhecimento de padrões para identificação de ataque de DNS. Revista Brasileira de Computação Aplicada (ISSN 2176-6649), Passo Fundo, vol. 9, n. 2, p. 99-110, jul. 2017. Disponível em: http://seer.upf.br/index.php/rbca/article/view/6279/4288; acesso em 13 jul 2022.
FIREEYE. Visualização de ataques ransomware em tempo real. 2022. Disponível em: https://www.fireeye.com/cyber-map/threat-map.html; acesso em 06 jul 2022.
FORNASIER, Mateus de Oliveira; SPINATO, Tiago Protti; RIBEIRO, Fernanda Lencina.Ransomware e cibersegurança: a informação ameaçada por ataques a dados. Recista Thesis Juris. E-ISSN: 2317.3580. 20 mai 2020. Disponível em: https://periodicos.uninove.br/thesisjuris/article/view/16739; acesso em 11 jul 2022.
GAFETY. O que é RaaS (Ransomware as a Service)? Artigo publicado em 23 mar 2021. Disponível em: https://gatefy.com/pt-br/blog/o-que-e-raas-ransomware-as-a-service/; acesso em 28 jul 2022.
KASPERSKY LAB. O que é o ransomware WannaCry? 2022A. Disponível em: https://www.kaspersky.com.br/resource-center/threats/ransomware-wannacry; acesso em 27 jul 2022.
KASPERSKY. O que são ataques de DDoS? 2022B. Disponível em: https://www.kaspersky.com.br/resource-center/threats/ddos-attacks; acesso em 28 jul 2022.
KOK, Sim Hoong; ABDULLAH, Azween; JHANJHI, Noor Zarman; SUPRAMANIAM, Mahadevan. Prevenção de Crypto-Ransomware usando um Algoritmo de Detecção de Criptografia. Computadores, nov. 2019, 8, 79; doi:10.3390/computadores8040079. Disponível em: http://paper.ijcsns.org/07_book/201902/20190217.pdf; acesso em 27 jul 2022.
KUMARI, Anjali; BHUIYAN, Md Zakirul Alam; NAMDEO, Jigyasa; KANAUJIA, Shipra; AMIN, Ruhul; VOLLALA, Satyanarayana. Proteção contra ataques de resgate: Uma Abordagem Criptográfica. Springer Nature Switzerland AG 2019. G. Wang et al. (Eds.): SpaCCS 2019, LNCS 11611, pp. 15-25, 2019.
https://doi.org/10.1007/978-3-030-24907-6_2; acesso em 27 jul 2022.
LAVADO, Thiago. JBS pagou US$ 11 milhões em resgate a autores de ataque ransomware. Matéria publicada em 09 jun 2021. Disponível em: https://exame.com/tecnologia/jbs-pagou-us-11-milhoes-a-autores-de-ataque-de-ransomware/; acesso em 06 jul 2022.
LEMA, Markus Carpeggiani de; FREITAS, Marcio. Ataques Ransomware. 5º. Seminário de tecnologia, Gestão e Educação. III Jornada Acadêmica & Simpósio de Egressos. ISSN 2675-1623. Faculdade e Escola Técnica Alcides
Maya. Rio Grande do Sul – maio 2021. Disponível em:
http://raam.alcidesmaya.edu.br/index.php/SGTE/article/view/326/318; acesso em 11 jul 2022.
LYNGAAS, Sean. Sistema de saúde da Flórida é invadido e dados de 1,3 milhão são expostos. 04 jan 2022. Disponível em: https://www.cnnbrasil.com.br/tecnologia/sistema-de-saude-da-florida-e-invadido-e-dados-de-13-milhao-sao-expostos/; acesso em 28 jul 2022.
MARIETTO, Maria das Graças Bruno. Sociedade da Informação e Geografia do Ciberespaço. INTERAÇÕES Revista Internacional de Desenvolvimento Local. vol. 2, n. 3, p. 29-36, set. 2001.
MARTON, Fábio. Anonymous descobre que “ataque ransomware” ao Ministério da Saúde era outra coisa; PF confirma. 10 dez 2021. Disponível em:
https://olhardigital.com.br/2021/12/10/seguranca/anonymous-pf-ransomware-ministerio-saude/; acesso em 06 jul 2022.
MASSENO, Manuel David; WENDT, Emerson. O ransomware na lei: apontamentos breves de direito português e brasileiro. Revista Eletrônica Direito & TI, vol. 1, n. 8, 2017. Disponível em: https://direitoeti.emnuvens.com.br/direitoeti/article/view/80; acesso em 11 jul 2022.
MEDEIROS, Breno Pauli; GOLDONI, Luiz Rogério Franco; BATISTA JR, Eliezer; ROCHA, Henrique Ribeiro da. O uso do ciberespaço pela administração pública na pandemia da COVID-19: diagnósticos e vulnerabilidades. Revista de Administração Pública. Rio de Janeiro, vol. 54, n. 4, p. 650-662, jul. – ago. 2020. Disponível em: https://www.scielo.br/j/rap/a/x3VKDBRYpkvNb8dmXN4rNyR/?lang=pt&format=pdf; acesso em 06 jul 2022.
MITRA, Amrita. What is ARP Spoofing? Figura 5. Publicada em março de 2017. Disponível em: https://www.thesecuritybuddy.com/data-breaches-prevention/what-is-arp-spoofing/; acesso em 28 jul 2022.
OLIVEIRA, Jéssica Cristina de. Ransomware – Laboratório de Ataque do WannaCry. Monografia [graduação em Engenharia de Software] apresentada à Universidade de Brasília – UnB Faculdade UnB Gama – FGA Engenharia de Software. Nov. 2018. Disponível em: https://bdm.unb.br/bitstream/10483/23052/1/2018_JessicaCristinaDeOliveira_tcc.pdf; acesso em 11 jul 2022.
OWAIDA, Amer. Agência de cibersegurança dos EUA adiciona a autenticação de fator único à lista de práticas inadequadas. Matéria publicada em 20 Oct 2021. Disponível em: https://www.welivesecurity.com/br/2021/10/20/agencia-de-ciberseguranca-dos-eua-adiciona-a-autenticacao-de-fator-unico-a-lista-de-praticas-inadequadas/; acesso em 06 jul 2022.
PEREIRA, Nicholas de Lucas Bastos; NEVES, Lucas Miranda. Ransomware e Phishing durante a pandemia Covid-19 (Coronavírus). Revista Tecnológica Fatec Americana, vol. 9, n. 01. 31 ago 2021. Disponível em: DOI: 10.47283/244670492021090167; Acesso em 11 jul 2022.
PHILOT, Daniel Rocha. Segurança da Informação: Ataques Ransomware e Proteção de Dados. Relatório de pesquisa na modalidade de Estudo de Caso apresentado ao Curso de Tecnólogo em Gestão da Tecnologia da Informação da Universidade do Sul de Santa Catarina. Palhoça (SC), 2021. Disponível em: https://repositorio.animaeducacao.com.br/bitstream/ANIMA/17754/1/DANIEL_ROCHA_PHILOT-Estudo_Caso-2021.pdf; acesso em 11 jul 2022.
PIMENTEL, Jose Eduardo de Souza; CABRERA, Diego Antunes; FORTE, Cleberson Eugênio. Ransomware: do surgimento aos ataques “as a service”. Congresso de Segurança da Informação das Fatec (FATEC SEG). I FatecSeg – Congresso de Segurança da Informação – 17 e 18 set 2021. Disponível em: https://www.fatecourinhos.edu.br/fatecseg/index.php/fatecseg/article/view/44/4; acesso em 11 jul 2022.
PPLWARE. Universidade com 157 anos fecha portas devido… a Ransomware. Matéria publicada em 11 mai 2022. Disponível em: https://pplware.sapo.pt/informacao/universidade-com-157-anos-fecha-portas-devido-a-ransomware/; acesso em
PRIVACY TOOLS. Tradicional universidade dos EUA, Lincoln College, fecha suas portas após um ataque ransomware. 2022. Disponível em: https://www.privacytools.com.br/tradicional-universidade-dos-eua-lincoln-college-fecha-suas-portas-apos-um-ataque-ransomware/; acesso em 06 jul 2022.
SILVA, Daniel Neves. Guerra Fria. 2022. Disponível em: https://mundoeducacao.uol.com.br/historiageral/guerra-fria.htm#:~:text=A%20Guerra%20Fria%20teve%20os,)%2C%20entre%201947%20e%201991; acesso em 12 jul 2022.
SILVA, Eduardo Araújo da. Ciberespaço e Cibercultura: Definições e Realidades Virtuais Inseridas na Práxis do Homem Moderno. 15 abr 2014. Disponível em: https://www.pedagogia.com.br/artigos/ciberespaco_cibercultura/index.php?pagina=3; acesso em 13 jul 2022.
SONICWALL. Visualização de ataques ransomware em tempo real. 2022A. Disponível em: https://attackmap.sonicwall.com/live-attack-map/; acesso em 06 jul 2022.
TECMUNDO – Ataque de ransomware desligou portas automáticas de prisão nos EUA. 11 jan 2022. Disponível em: https://www.tecmundo.com.br/seguranca/231807-ataque-ransomware-desligou-portas-automaticas-prisao-eua.htm; acesso em 06 jul 2022.
TIC NEWS. Senado norte-americano aprova pacote de cibersegurança. 10 03 2022. Disponível em: https://www.apdc.pt/noticias/atualidade-internacional/senado-norte-americano-aprova-pacote-de-ciberseguranca; acesso em 29 jul 2022.
APPENDIX – FOOTNOTE
2. International Business Machines.
[1] Technologist in Information Technology Management. ORCID: 0000-0002-5179-3114.
Sent: August, 2022.
Approved: August, 2022.