OLIVEIRA, Geveson de Souza [1]
PINTO, Aurílio Guimarães [2]
FREITAS, Caio Guimarães [3]
ALMEIDA, Cristiany Caliri de [4]
LEITE, Francisco Canindé da Silva [5]
SILVA, Francisco Eronildo da [6]
RIBEIRO, Dallas dos Santos [7]
MORAIS, Gilvanete Melo de [8]
PERES, Paulo Júnior de Jesus [9]
OLIVEIRA, Geveson de Souza; et.al. Free Software as a Secure Solution for Corporate Information Processing. Multidisciplinary Scientific Journal. Edition 07. Year 02, Vol. 02. pp. 47-57, October 2017. ISSN:2448-0959
summary
In this research, it is demonstrated that in addition to being more transparent, free software can be used in a practical way in companies instead of proprietary software. The data used were collected from a trial scenario, from which four (4) free tools were tested: OPENLDAP, SQUID, ZIMBRA and CACTI. In the end, it was proven that the use of these free tools are vital for the survival of a company in order to protect the availability, integrity, and confidentiality of business information.
Keywords: Free Software, Information Security, Proprietary Software.
1. Introduction
Each day the business areas of organizations are using Information Technology (IT) services to support their strategic and operational activities. In this sense, the importance of IT services and the use of tools that help the growth of a company grow considerably.
The organizations have been seeking to migrate their systems as a business strategy, seeking a collaborative development model such as free software. Many companies use unlicensed software and thus fall into the world of software piracy, being targets of audit bodies.
This article is organized in six more sections. In section 2, denominated "Methodology", the comparatives between the proprietary tools and the free tools are approached. In section 3, "Information Security in Business", addresses the objectives of information security, as well as encryption of data and communication networks and related work. Section 4, "Scenario", presents the scenario description, the test methodologies, as well as the tests performed. Sections 5 and 6 present the results obtained and the analysis of the results. The conclusions and perspectives are discussed in section 7.
2. Methodology
The present work has its methodology based on bibliographic review, case study of success, and through free tool tests, through a scenario of experimentation.
2.1 Proprietary Software X Free Software
According to Gonçalves (2007), proprietary software is one whose copy, redistribution or modification is to some extent prohibited by its owner. And to use, copy or redistribute one must request permission from the owner, or pay to be able to do so.
According to Silveira (2004), Free Software refers to the freedom of users to execute, copy, distribute, study, modify and improve the software.
2.2 Free Tools
According to Oliveira Júnior (2006), there are several free software projects in the most varied applications: business, finance, project management, software development, internet, education, text editors etc., as well as business world technologies such as: CRM (Customer Relationship Management System), ERP (Integrated Management System), Data Warehouse and OLAP (online analytical processing).
Table 1 describes the free tools that will be used in this work, as well as their comparison with proprietary tools.
Table 1 – Comparison of proprietary software with free software
| Kind of service | Software Owner | Free software |
| Directory Service | Active Directory | OpenLDAP |
| Internet Access Control | WinGate | Squid |
| E-mail Service | Exchange | Zimbra |
| Network Monitoring Service | PRTG Network Monitor | Cacti |
The free tools cited in Table 1 are some software used for the management and control of an IT infrastructure.
3. Information Security in Companies
According to Fontes (2006), Information Security can be defined as a set of norms, policies, procedures and other actions that lead to the protection of assets that contain information and that enable the mission of an organization to be achieved making the business viable. It minimizes the risks to the business and consequently losses that jeopardize its operation and the return of the investment of its shareholders.
Information is an asset that, like any other important asset, is essential to the business of an organization and therefore needs to be adequately protected. This is especially important in the increasingly interconnected business environment.
3.1 Information Security Objectives
According to Diógenes (2011), Information Security has three basic concepts that are considered the pillars of Information Security and should be the foundation of any security plan. According to Beal (2008), compliance with measures that guarantee the protection of information in these aspects means that information is relatively safe.
3.1.1 Data Encryption and Communication Networks
According to the Center of Studies, Response and Treatment of Security Incidents in Brazil (2006), cryptography, considered as the science and art of writing messages in encrypted or coded form, is one of the main security mechanisms that can be used to protect against the risks associated with using the Internet.
Several security mechanisms are implemented to increase Information Security in data transmission. According to the Internet Security Primer (2006), security mechanisms such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols that, through encryption, provide confidentiality and integrity in communications between a client and a server , and can also be used to provide authentication.
3.2 Related Work
In the scope of this work, we observed a range of information-related works in diverse segments that were researched with the purpose of enriching and producing theoretical basis for this work. Among them, the following two works are highlighted:
The first work, written by Miranda (2011) and entitled "The use of free software as an alternative for small and medium enterprises", which aims to show through a case study, the use of technologies based on free software.
The second work, a dissertation written by Mendes (2006), makes a study on "Free Software and Technological Innovation", whose objective is to discuss the potential of free software to foster technological innovation, through its protection regime to intellectual property , in developing countries, with Brazil as a reference.
4. Scenario
The experimentation scenario was prepared with the intention of applying the proposed methodology and performing the laboratory tests of the free tools used for this work.
4.1 Description of the Scenario
For the phases of free software tests, four tools were used.
Table 2 shows the configurations of the computers and systems used in this study for free tool testing activities. An equipment was used in which seven virtual machines were created.
Table 2 – Equipment and systems used
| Equipment | Description |
| Host Computer | Mac Apple OS X with Intel Core i5 Processor, 2.5Ghz, 4GB RAM, 500GB HD. |
| Virtual Machine 1 (Server 01) | Linux Debian 7.6.0, 2GB RAM, 60GB HD. |
| Virtual Machine 2 (Server 02) | Linux Debian 7.6.0, 2GB RAM, 60GB HD. |
| Virtual Machine 3 (Server 03) | Linux Debian 5.0, 2GB RAM, 60GB HD. |
| Virtual Machine 4 (User 2) | Ubuntu 14.04, 1GB RAM, 8GB HD. |
| Virtual Machine 5 (User 3) | Ubuntu 14.04, 1GB RAM, 8GB HD. |
| Virtual Machine 6 (User 4) | Ubuntu 14.04, 1GB RAM, 8GB HD. |
| Virtual Machine 7 (User 5) | Ubuntu 14.04, 1GB RAM, 8GB HD. |
It was used only one equipment (a host computer) to create the experimental scenario, it is emphasized that in the host computer was configured a small internal network with seven virtual machines, star topology, in which there are three Debian servers, and four Ubuntu Desktop machines.
The virtualisation software, distributed free of charge on the GPL license, VirtualBox version 4.3.20, of the multinational company Oracle Corporation was used. VirtualBox is an Oracle virtualization program that lets you install and run different operating systems on a single computer.
4.2 Test Methodology
The methodology for performing the tests consists of using virtual machines on a host computer to configure a small internal network with seven virtual machines of star topology in which there are three Debian servers and four Ubuntu desktop machines . The tests performed will check the usability of the free tool in an internal network structure, such as user authentication tests on a directory system, Internet access through Proxy, user access to internal e-mail, and user access to the monitoring of an internal network.
4.3 Operating Systems Servers and Clients
As a server operating system, the free non-commercial Debian GNU / Linux system was adopted. For client stations the Ubuntu operating system was adopted, Linux distribution based on Debian, open source and maintained by the company Canonical Ltd. The Ubuntu operating system is an intuitive interface system and looks like the Microsoft Windows operating system.
In Server 01, the free software tools "OpenLDAP" and "Squid" were installed. Essential tools for the control of logical access of users of information technology. "OpenLDAP" is a tool for controlling user access to information systems. And the "Squid" tool will function as a web browsing server, through user authentication.
In Server 02, the free software tool "Cacti" was installed. Tool for checking and monitoring a computer network. This free code tool collects and displays information about the state of a computer network through graphics.
In Server 03, the free software tool "Zimbra" was installed. E-mail and collaboration software tool, group calendar, contacts, instant messaging, file storage and web document management.
4.4 Tests performed
In this part, we highlight some points regarding the tests performed with the proposed free tools, demonstrated, through a scenario of experimentation according to the following specification:
a) OpenLDAP
The "OpenLDAP" tool was installed and configured on a Debian server, as well as the split access tests of client machines, as shown in Figure 1.
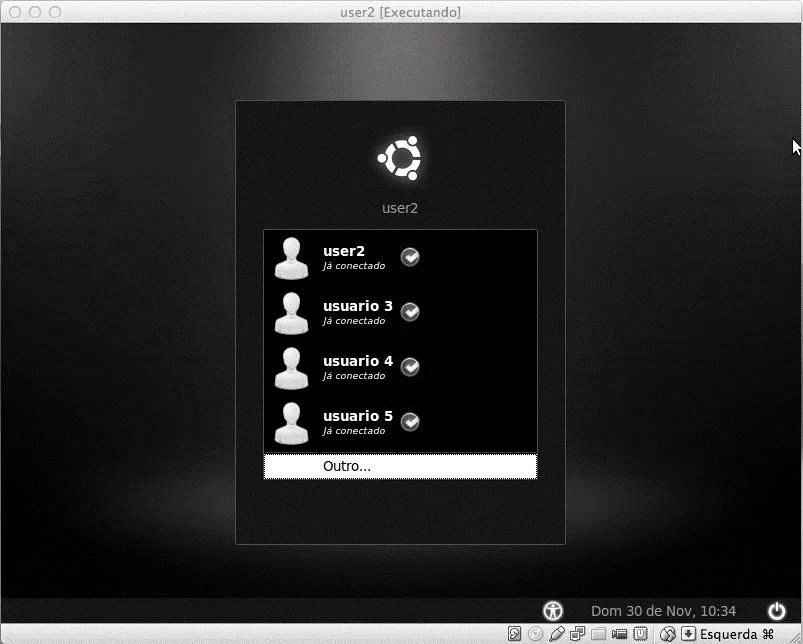
Tests were performed on both the "LDAP" user access part and data sharing tests in the "LDAP" directory. All client machines were able to authenticate to the "LDAP" base, as shown above. To increase security, the open source library "OpenSSL" has been installed that implements the basic cryptographic functions.
b) Squid
The Squid tool has been installed and configured on a Debian server, as well as the split access testing of client machines.
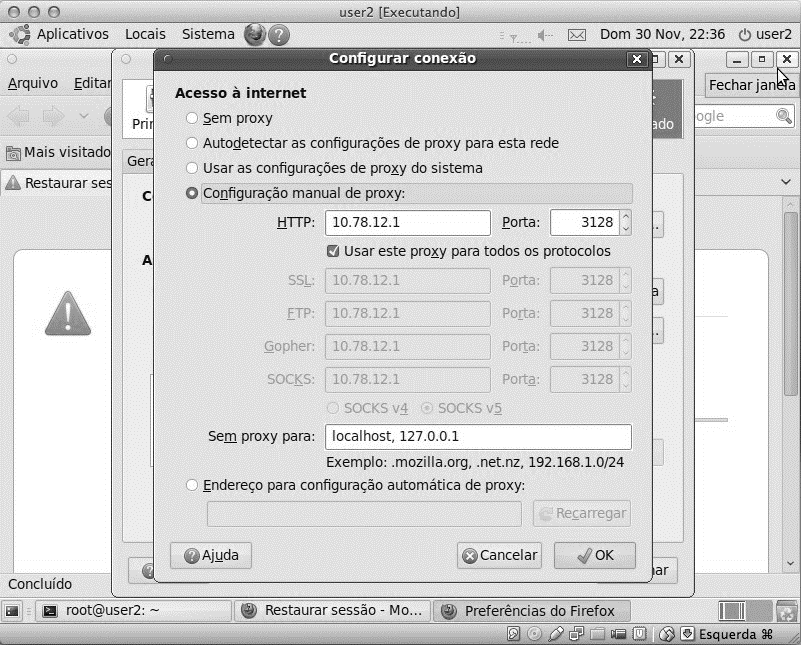
To increase security, the "NatACL" tool was installed for authentication of internet access by registered users.
c) Zimbra
The "Zimbra" tool has been installed and configured on a Debian server, as well as the split-access testing of client machines.
Figure 3 shows the Administrative Console screen of the tool "Zimbra", where all the configuration of the electronic mail system is done, as well as the creation of the users of the system.
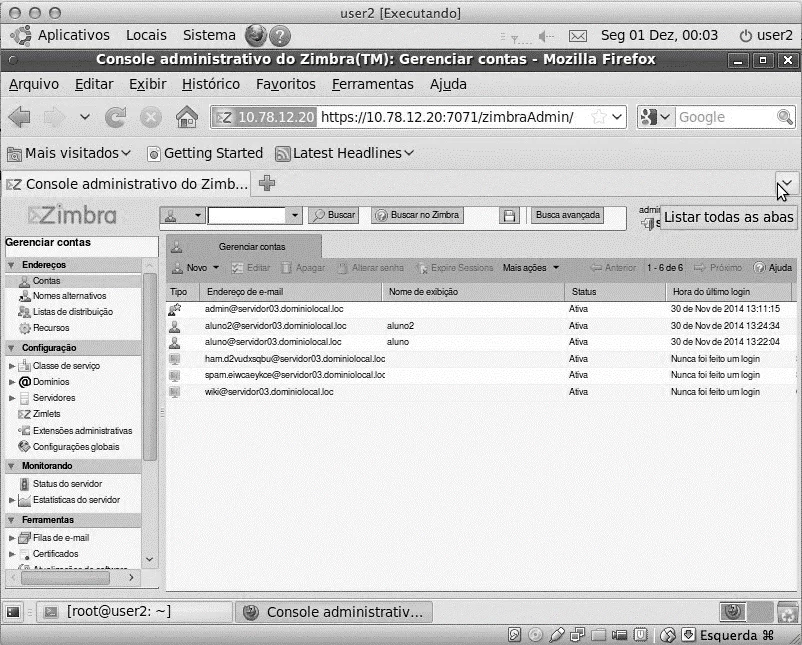
d) Cacti
The "Cacti" tool was installed and configured on a Debian server, as well as the part access tests of client machines, as shown below.
The system can be accessed by registered users, thus making use of the tool for displaying and monitoring the internal network.
To increase security, the use of Cacti for information access via the "SNMP" protocol was tested.
5. Results obtained
It was assumed a scenario of experimentation, in which a topology network of the star type was represented with 4 (four) client users and 3 (three) servers, thus simulating a small internal network.
The test performed in the "OpenLDAP" tool consisted of authenticating the users in the LDAP database. The 4 (four) users used in the experiment scenario were able to authenticate to the base and use the "LDAP" directory without any problem.
The test performed in the tool "Squid" consisted of using the tool as a proxy in which client machines access the Internet through this "Proxy". The four (4) users used in the experimentation scenario were able to navigate the internet through the use of the "Squid" tool without any problem.
The test performed in the tool "Cacti" consisted of using the tool through a browser to view and monitor the internal network created. The four (4) users used in the experiment scenario were able to access the tool to view and monitor the internal network created.
The test performed in the tool "Zimbra" consisted of using the tool as electronic mail for the processing of corporate information through e-mail messages. The four (4) users used in the experimentation scenario were able to access the e-mail tool and process information between them.
Table 3 – Pros and Cons
| Tool | Pros | Against |
| OpenLDAP | Immediate configuration without having to stop Open Ldap; Easy configuration; Protection against unauthorized access. |
Little documentation availabl e; Incompatibilities with other tools in the case of a migration; Redundancy of information. |
| Squid | Control of web connect ions; Connection sharing between users ; Better response time. |
Little documentation available ; Does not support other types of services like smtp, pop3, internet games, etc . Low security in protocols and applications. |
| Zimbra | Easy administration of users; Easy configuration and web interf ace; Scalability and ease of maintenance. |
Little documentation availabl e; Slow synchronizat ion; Incompatibilities with other tools in the case of a migration. |
| Cacti | It is flexible and adapts to various needs; Robust and easy to use; Generated graphics are customizable. |
Little documentation ava ilable; Does not have automatic network discovery devices (must be added m anually); Problem reporting service failures. |
In the Table above the advantages and disadvantages of the free tools used in this work are shown.
6. Analysis of Results
The "OpenLDAP" tool installed on a Debian server guaranteed user access control to the "LDAP" directory. Assuring thus, that the purpose of authentication in the base "LDAP" has been fulfilled of satisfactory form.
The "Squid" tool installed on a Debian server, guaranteed the control of internet access, through authentication, of the users registered in the Squid system. The Squid system has fulfilled its role as an intermediary between the user of a workstation and the Internet, ensuring security, administrative control and caching service that stores pages previously visited on the server.
The tool "Zimbra" installed on a Debian server, guaranteed the control of access to electronic mail by users of the system. The "Zimbra" e-mail system can be used as an enterprise e-mail server and can be integrated with the "OpenLDAP" system. The tool behaved in a satisfactory manner, fulfilling all the requirements of a proprietary software e-mail.
The "Cacti" tool installed on a Debian server, guaranteed access control to the network monitoring tool through the users registered in the system. The tool collected and displayed information about the state of the internal network through graphs, as well as being robust, flexible and easy to use.
The following table shows the results obtained regarding the complexity of installation, usability and safety of each tool. The measurement is classified as High, Medium, and Low.
Table 4 – Classification of tools
| Tool | Practicality | Efficiency | Safety |
| OpenLDAP | Average | Average | High |
| Squid | Low | High | Average |
| Zimbra | Average | High | High |
| Cacti | Average | Average | High |
Conclusion
It was observed that due to the constant use of proprietary software by companies, there was a need to acquire the license of the proprietary software, which greatly affected the values for the companies, due to the high costs of software licenses. Given this, it has been demonstrated that the use of free software, instead of proprietary software, is an alternative for these companies.
It was also observed that in addition to being more transparent, free software can be used in a practical way in companies to replace proprietary software, in order to protect the availability, integrity, and confidentiality of corporate information.
It should be noted that the use of free software grants users the freedom to change and modify, through the availability of the source code, making it possible to adapt the software to the specific objectives of each person or company. Any software, be it proprietary or free, is subject to errors in its development. In the case of free software, when an error is discovered the same is fixed by the free software community, which are people scattered all over the world, which increases the possibility of immediate correction. This does not occur with proprietary software, as an error in the source code may take days or even months to be found and corrected.
By performing the tests and analyzing the results, it was observed that the tools were used in a more transparent way than the proprietary software, as well as maintained in a stable way during the tests and fulfilled with the functionalities that it was proposed.
Therefore, the objective proposed by this work was reached by demonstrating that the proposed free tools can be used as a secure solution for the information processing. And, finally, safeguarding the availability, integrity and confidentiality of corporate information.
References
BEAL, Adriana. Information security: principles and best practices for protecting information assets in organizations. São Paulo: Atlas, 2008.
CENTER OF STUDIES, RESPONSE AND TREATMENT OF SAFETY INCIDENTS IN BRAZIL. Security booklet for internet. Version 3.1, 2006. Available at: <http://cartilha.cert.br/>. Accessed on: 08 Oct. 2014.
DIÓGENES, Yuri; MAUSER, Daniel. Security + certification: from practice to the SYO301 exam. Rio de Janeiro: Novaterra, 2011.
SOURCES, Edison. Information security: the user makes a difference. São Paulo: Saraiva, 2006.
GONÇALVES, Rodrigo Moura. Application of an open source CRM web tool. Santa Catarina. 2007. 68 p. Available at: <https://projetos.inf.ufsc.br/arquivos_projetos/pro jeto_650 / TCC% 20-% 20Rodrigo% 20Moura.pdf>. Accessed on: 18 Oct. 2014.
MENDES, Cássia Costa. Free software and technological innovation: an analysis from the perspective of intellectual property. 2006. 282 p. Dissertation (Master's in Economic Development) – Post-graduation in Economic Development, State University of Campinas, 2006. Available at: <http://www.bibliotecadigital.unicamp.br/document/?code=vtls000378144>. Accessed on: Oct 20. 2014.
MIRANDA, Kermit Barbosa. The use of free software as an alternative for small and medium enterprises: to present alternative technologies used in the computational environment of small and medium enterprises in the industry, commerce and services sectors based on the free software platform. 2011. 62 p. Monography (Post-Graduation in Network Administration and Information Systems). Faculdade Fucapi, 2011.
OLIVEIRA JÚNIOR, Raul Simas de. Acceptance Assessment of Integrated Management Systems. Annals of the First Information Administration Meeting, Florianópolis-SC, 2007.
SILVEIRA, Sérgio Amadeu. Free software: the struggle for freedom of knowledge. São Paulo: Perseu Abramo Foundation, 2004.
[1] He holds a postgraduate degree in Information Security Management from Faculdade FUCAPI, and is a public servant of the Superintendence of the Manaus Free Zone – SUFRAMA, in the position of Technical Administrative Analyst – Information Technology.
[2] Graduated in the Computing area, he is a public servant of the Manaus Free Trade Zone Superintendence – SUFRAMA, in the position of Technical Administrative Analyst – Information Technology.
[3] Graduated in the Computing area, he is a public servant of the Manaus Free Trade Zone Superintendence – SUFRAMA, in the position of Technical Administrative Analyst – Information Technology.
[4] Graduated in the Administration area, she works as a public servant of the Superintendence of the Manaus Free Zone – SUFRAMA, in the position of Administrator.
[5] Graduated in the Computing area, he is a public servant of the Manaus Free Trade Zone Superintendence – SUFRAMA, in the position of Technical Administrative Analyst – Information Technology.
[6] Graduated in the Computing area, he is a public servant of the Manaus Free Zone Superintendence – SUFRAMA, in the position of Administrative Technical Analyst – Information Technology
[7] Graduated in the Computing area, he is a public servant of the Manaus Free Trade Zone Superintendence – SUFRAMA, in the position of Technical Administrative Analyst – Information Technology.
[8] Graduated in Economics, she is a public servant of the Superintendence of the Manaus Free Zone – SUFRAMA, in the position of Economist.
[9] Graduated in the Computing area, he is a public servant of the Manaus Free Trade Zone Superintendence – SUFRAMA, in the position of Technical Administrative Analyst – Information Technology.